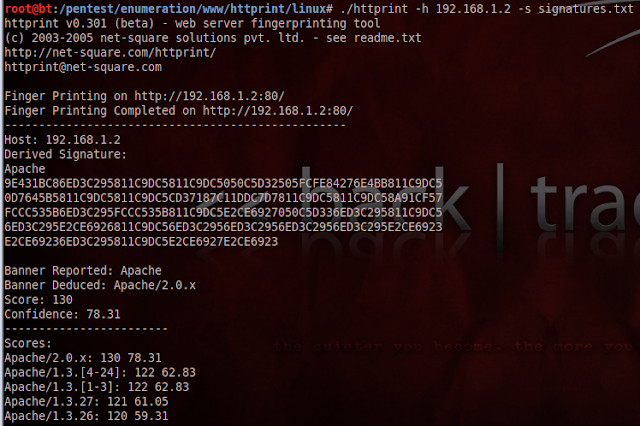
hexinject is capable to inject any packet to the network, which we construct on our own in hex. The tool doesn't do any verification, so it will send even a sentence like 'jaj de finom ez a leves' (this soup is really tasty - in Hungarian). Thus if we screw up the various protocols' structure another software won't be able to understand it. It has a sniffing mode, where we can listen to the network traffic. It's quite hard to use on its own, but using pipes or scripts it can be really useful.
Examples:
hexinject -s -i eth0 -> sniffing eth0 interface
hexinject -s -i eth0 -r -> output in raw format
hexinject -s -i eth0 -r | strings -> using strings
hexinject -s -i eth0 -r | strings | Host -> filtering on hosts
echo 'Jaj de finom ez a leves' | hexinject -p -i eth0 -r -> sending a custom string to the network
This will create a packet like this:
The possibilities are unlimited, it's worth to read the documentation and other examples on its webpage: