macchanger can change the MAC address on a network interface, it works, when the interface is down:
macchanger -m 12:22:33:44:55:66 wlan0
We can set the multicast bit on the MAC address to 1 with this tool, which is actually make sense.
Example:
Good: 12:22:33:44:55:66
Bad: 11:22:33:44:55:66
Sunday, October 30, 2011
WiFi: Discovering hidden SSID
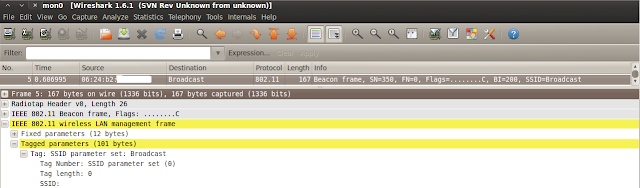
Let's see why it means exactly 0 (zero) security if we hide our wireless' network SSID, hoping that no one can find it. People usually think that if they don't broadcast their SSID, then others can't connect to their network.
The AP still broadcasts Bacon frames, but without the SSID, so we see that something is there, but we don't know what. Here is how does it look in Wireshark and airodump-ng:
We can place our wifi card to monitor mode this way:
root@bt:~# airmon-ng start wlan0
This creates a mon0 interface which will belong to the wlan0 NIC, and we can't use wlan0 during this time. We can start monitoring with airodump-ng:
We have two options:
1. We wait passively for a client to connect to the wireless network, cause then there will be a Probe request/response message exchange, where we will see the SSID in the response (this is the standard).
2. If we are inpatients, we can disconnect the clients with sending "deauth" packets with the AP's MAC address, thus causing them to reconnect, and we can reveal the SSID. Here it is:
root@bt:~# aireplay-ng -0 2 -a 06:24:B2:D8:3B:17 mon0
where:
-0 - deauth packet
2 - number of packets
-a - AP MAC address
and the interface.
The result: we get the SSID.
So it doesn't worth doing ourselves additional work with hiding the SSID.
Book: BackTrack 5 Wireless Penetration Testing Beginner’s Guide
I swear I don't get money from the publisher, but others don't publish such books. :-) Another interesting book have been released by PacktPub about Backtrack:
BackTrack 5 Wireless Penetration Testing Beginner’s Guide
Based on the table of contents, it's everything about WiFi security testing.
You can buy it here and download chapter 6 for free:
http://www.packtpub.com/backtrack-5-wireless-penetration-testing-beginners-guide/book
It can be downloaded in both PDF and ePUB formats, as their other books.
BackTrack 5 Wireless Penetration Testing Beginner’s Guide
Based on the table of contents, it's everything about WiFi security testing.
You can buy it here and download chapter 6 for free:
http://www.packtpub.com/backtrack-5-wireless-penetration-testing-beginners-guide/book
It can be downloaded in both PDF and ePUB formats, as their other books.
Saturday, October 29, 2011
Backtrack basics 8. - connecting to WiFi network with iwconfig
With the use of iwconfig we can connect to open and WEP protected wireless networks from the command line.
Open networks:
iwconfig wlan0 essid WLAN_test
iwconfig wlan0 essid WLAN_test key AAAABBBBCC
Where wlan0 is the name of the wireless interface, WLAN_test is the SSID and AAAABBBBCC is the WEP key.
Realtek RTL8187L - SIOCSIFFLAGS: Unknown error 132
WiFi NIC cards, which has Realtek RTL8187L chipset inside (eg Netgear WG111v3) often produce the following error when we try to turn it OFF and then ON: "SIOCSIFFLAGS: Unknown error 132". This is a bug. The solution is running the following small script:
rmmod rtl8187rfkill block all
rfkill unblock all
modprobe rtl8187
rfkill unblock all
ifconfig wlan0 up
Subscribe to:
Posts (Atom)